CyberHive Trusted Cloud

Why use Trusted Cloud?
Save up to 40% overhead cost per environment by centralising security access and availability, and simplify account infrastructure saving on average two-person months per project by reducing accreditation time, while delivering the same security benefits.
Significantly reduce the time it takes to detect and locate data breaches down to seconds. Rapid detection has a very strong case when considering where to prioritise efforts to increase cyber resilience. The less time hackers and malicious insiders are left to probe around your network unchallenged the better.
The infrastructure is designed to handle a range of different workloads without material changes to the environment. Automated deployment minimises potential installation errors and a high baseline security posture reduces the examination surface for re-accreditation.
Enable sensitive workloads on public cloud infrastructure
Secure hosting from CyberHive uses Terraform and Ansible to provide a configuration-as-code environment designed to deploy and operate secure multi-account, multi-region, standardised secure public cloud environments such as AWS.
Secure environments are automatically deployed and configured and can be used to host and operate a wide range of different workload accounts without the need for material infrastructure changes.
The validation and assurance in the platform means it is not only fast to deploy but the scope and associated costs and time for further accreditation for any workload accounts is greatly reduced as the base security of the platform is a given.
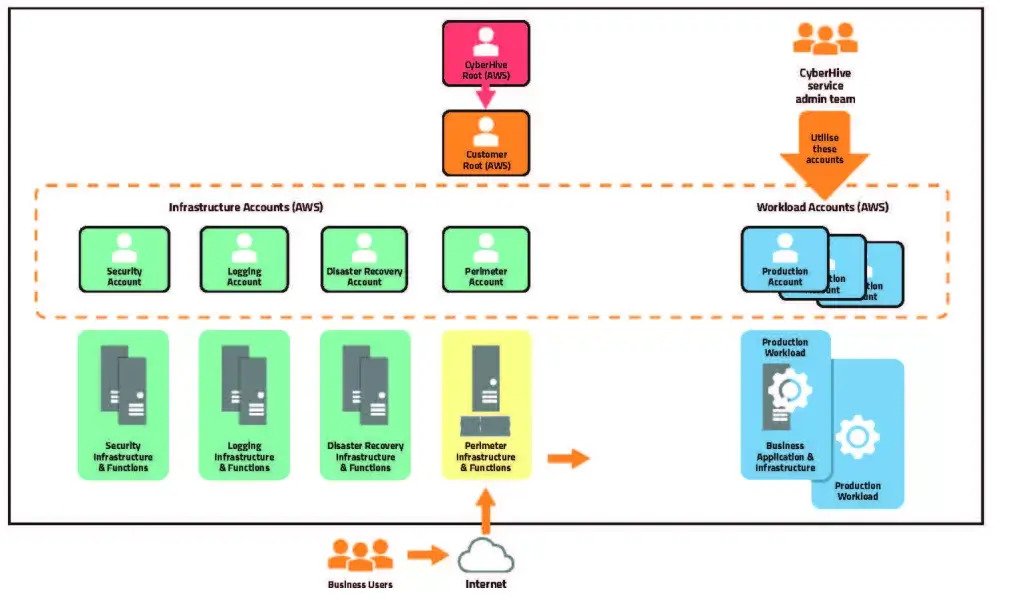
Our infrastructure delivers segregation of duties as standard. It restricts access from the workload accounts to the administrative and functional accounts. It audits the configuration of the cloud hosting accounts and services along with administrative actions and controls, and audits network access to and from the workload accounts. It provides automated scheduling to start and stop workload accounts assisting budget control and provides automated immutable backups of EC2 and RDS data.
In summary CyberHive secure hosting delivers a secure, faster, more agile deployment solution for IaaS projects with best practice security controls in an automated, repeatable fashion delivering both cost and time savings.
Detect
Detect malicious attackers in seconds not months, no matter how they got in. With Trusted Cloud server security, any unauthorised code or modifications will be identified and flagged in seconds. Action can then be taken to stop the cyber criminal in their tracks before any damage can be done.
Discover
Discover attacks that would bypass your defences and go undetected by conventional cyber security technologies. Trusted Cloud uses hardware-backed distributed allow-lists to check all code and configuration on your servers in real time. Any changes, no matter how small or carefully disguised will be detected in seconds.
Protect
Protect your systems from being compromised. Prevent security lapses, social engineering attacks and even malicious acts by employees or 3rd party service provider. Humans are always the weakest link. By deploying Trusted Cloud, you can eliminate data breaches even if they start with a slip-up by an authorised system administrator.
Avg. breach cost
Time to detect and contain
Human element
Ransomware growth
The solution – CyberHive Trusted Cloud
By harnessing a unique combination of hardware-based cryptography and allow-listing – Trusted Cloud gives you the best server protection available.
Trusted Cloud is unique, it combines advanced allow-listing technology with the power of a Hardware Security Module, a dedicated micro-controller that secures hardware through advanced cryptography. Allow-listing protects servers by ensuring that only approved code is running.
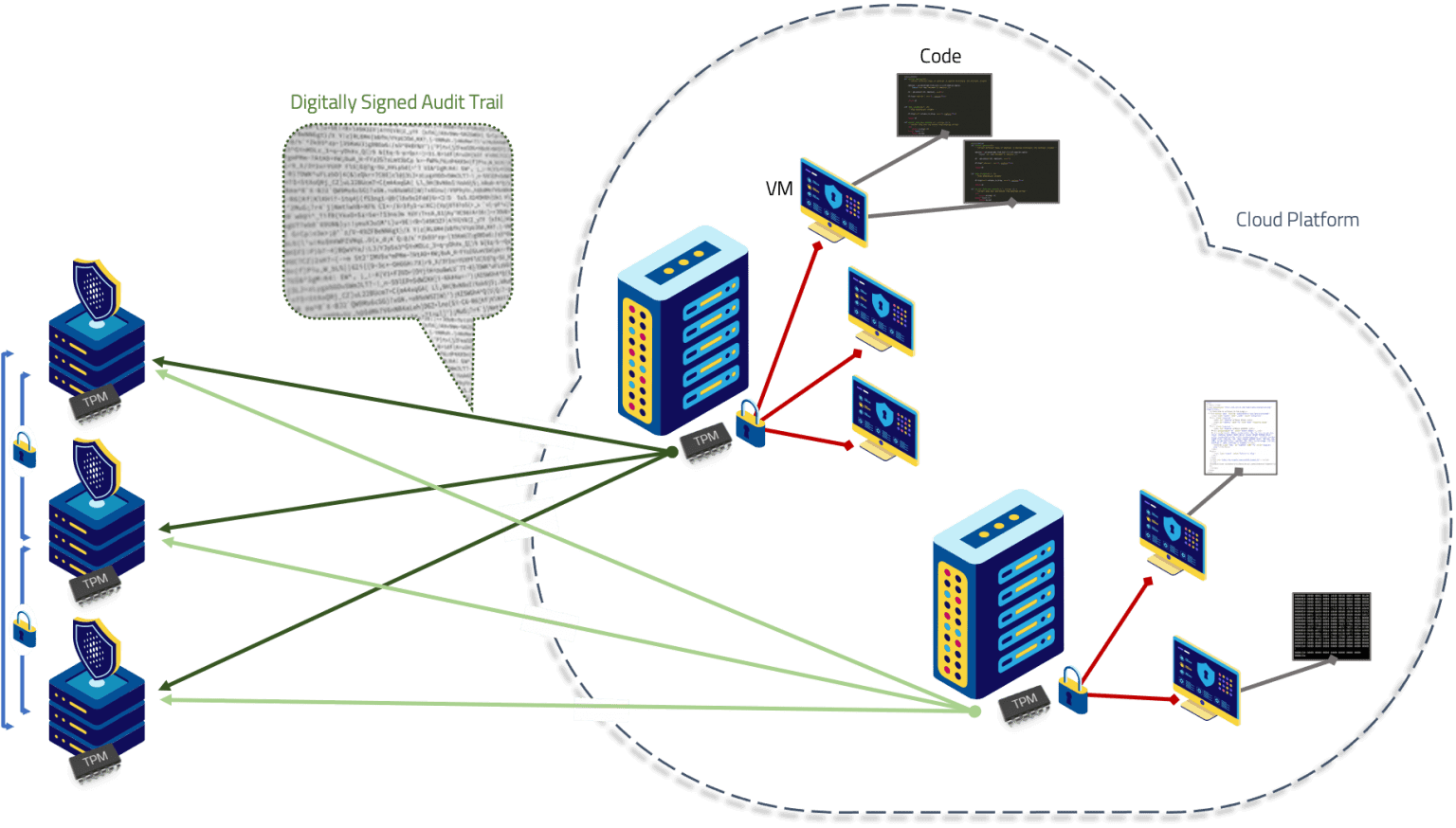
However, the need to periodically transmit a list of what is running to a verification service makes this approach vulnerable. During an attack, lists can be intercepted and altered by external hackers or malicious insiders. They can effectively cover their tracks, making it appear as if everything is normal.
Our developers have broken new ground for allow-listing by harnessing the unique properties of Intel’s Trusted Platform Module (TPM) to digitally ‘sign’ lists.
Every few seconds this data is sent to a verification server to confirm that not even a single line of unauthorised code is running, offering robust defence against single points of failure, both technical and human.
Trusted Cloud can be deployed to protect your data in the cloud and on servers within your own data centre. With our unique trust verification technology you can check the ‘trusted’ status of your servers yourself. You no longer need rely on assurances from your cloud provider that your data is secure.
By rolling out Trusted Cloud you can significantly reduce the costs of security and compliance. Our technology detects threat actors before they have a chance to do any damage.
Book a demo
Contact the team to learn more about CyberHive secure hosting for sensitive workloads

