
Why Zero Trust Security is Crucial to Business Security
Why Zero Trust Security is Crucial to Business Security

Traditional VPNs are no longer sufficient to protect against sophisticated cyber threats. It’s time to upgrade to a more secure, efficient, and future-proof solution. Zero trust network access (ZTNA) is the next generation of network security.
ZTNA is a strategic approach to network security that eliminates the traditional trust assumptions within network environments. Instead of assuming everything behind the corporate firewall is safe, ZTNA asserts that trust must be earned, regardless of location.
Replace VPNs with ease
Say goodbye to the vulnerabilities and complexities of VPNs. Our ZTNA solution, CyberHive Connect, enables seamless communication between devices and applications while making them invisible on the internet, drastically reducing your attack surface. Leveraging cutting-edge post-quantum cryptography, we ensure your data remains secure against even the most advanced threats.
Fast and frictionless deployment
Unlike other SaaS solutions, our software is truly frictionless. Deploy it in minutes without the need for a complete overhaul of your existing infrastructure. This means no costly disruptions or downtime – just immediate, robust security.
Optimised for the toughest conditions
Our solution excels in challenging environments. Independent tests by Viasat revealed that our software outperforms WireGuard and OpenVPN, offering superior performance with lower overhead. Toshiba demonstrated our software’s resilience by maintaining telemetry streams in networks with over 90% packet loss. Whether you’re in defence, intelligence, or managing critical national infrastructure, CyberHive Connect is built to handle it all.
Proven performance
Our software has been rigorously tested and proven to be more performant under extreme conditions. This ensures that your operations remain secure and uninterrupted, even in the most demanding scenarios.
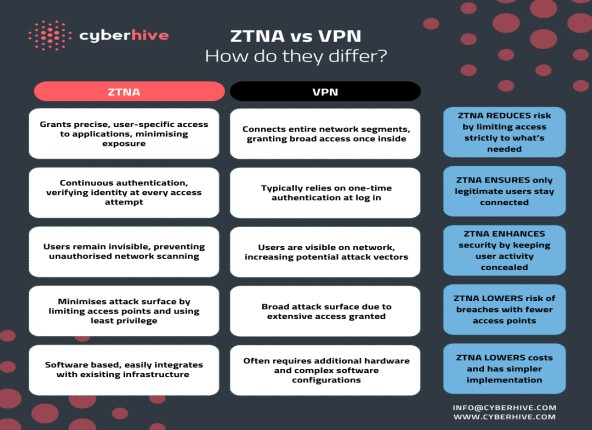
Here is our guide on why zero trust network access (ZTNA) is the superior choice over traditional VPNs. As organisations continue to face sophisticated cyber threats, it’s essential to adopt security measures that provide robust protection while being cost-efficient.
On the left, we compare ZTNA and VPN across five critical areas to help you understand why ZTNA stands out as the best option for your cyber security needs.
In the UK, regulations around ZTNA are influenced by the National Cyber Security Centre (NCSC), which provides guidance on implementing zero trust principles. The NCSC emphasises the importance of a zero trust approach, particularly in the context of the government’s Minimum Cyber Security Standard (MCSS) and other regulatory frameworks like GDPR.
Key aspects include:
The UK’s approach aligns closely with global best practices, encouraging organisations to adopt a zero trust architecture (ZTA) to enhance their cyber security posture.
NIST Special Publication (SP) 800-207 outlines the principles and implementation guidelines for Zero Trust Architecture (ZTA). It was developed by the National Institute of Standards and Technology (NIST) to provide a comprehensive framework for adopting zero trust principles:
These are the basic assumptions for network connectivity and form the understanding on which a ZTNA should be designed:
CyberHive Connect meets all of these design points.
NIST SP 800-207 is applicable to a wide range of organisations, from government agencies to private companies. It is particularly relevant for those looking to modernise their cyber security strategies beyond traditional perimeter defenses.
The guidelines are crucial because they:

Don’t wait until it’s too late. Upgrade to our ZTNA solution, CyberHive Connect today and experience unparalleled security and performance.
Protect your organisation from evolving cyber threats with a solution designed for the most critical and challenging environments.
Contact us now to schedule a demo, or better yet – try it for free.
Secure your future, now.
We think differently. Working in partnership with our clients our cutting-edge products deliver agile, innovative solutions to protect against cyber security attacks.
Dive deeper into how our ZTNA can revolutionise your security.

Why Zero Trust Security is Crucial to Business Security

Take a look closer at how ZTNA can transform your organisation’s security posture
If you have a question or would like some more information, contact us today.